All user passwords are set through https://trueyou.nebraska.edu/ and must conform to the following rules.
Number of possible passwords (16,777,216) = 2 raised to the power of net total bits of entropy (2 ^ 24)
Limit of 16,384 tries = number of possible passwords / assurance level requirement (16,777,216 / 1,024)
Credentials are synchronized across both Active Directory and LDAP, resulting in 30 possible password attempts in a 5 minute period.
Authentication failures are tracked for the two authentication stores (Active Directory and LDAP), via our Splunk log aggregation system. Once authentication failures are collected in the Splunk Indexer (Accumulator), a script runs every 10 minutes to monitor the failed authentication attempts and password resets. Authentication failures and password resets are stored in the Authentication Failure Monitor database, which is replicated in two locations. In that 10 minute period, a single user may have had 60 attempts across AD & LDAP.
The code for the authentication failure monitor is available on GitHub: https://github.com/saltybeagle/AuthNFailures
Three searches are monitored:
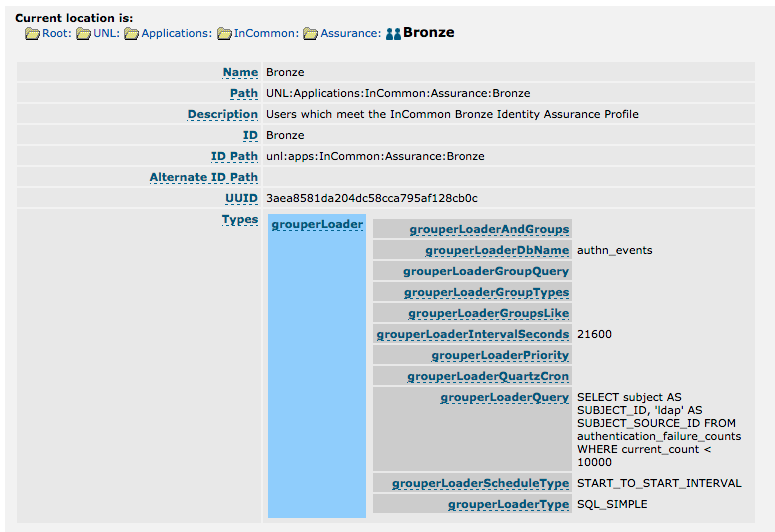
Grouper is used to monitor the Authentication Failure Database, and synchronize the list of users that have a credential which meets the Bronze credential requirements. A user must have a password reset event stored in the Authentication Failure Database, and have had no more than 10,000 authentication failures, to be included in the Bronze credential group.
The Grouper Loader Job runs every 6 hours via a START_TO_START_INERVAL.
Password Complexity Rules:
- Must be between 8 and 127 characters in length
- Must not contain values of attributes: accountId, email, lastname, firstname, fullname
- Must meet at least 3 of the 4 following conditions
- Contain at least 1 Numeric character
- Contain at least 1 Special character, ie:
~!@#$%^&*()_+=-`{}[]|\:";'<>,.?/ - Contain at least 1 Uppercase letter
- Contain at least 1 Lowercase letter
Number of possible passwords (16,777,216) = 2 raised to the power of net total bits of entropy (2 ^ 24)
Limit of 16,384 tries = number of possible passwords / assurance level requirement (16,777,216 / 1,024)
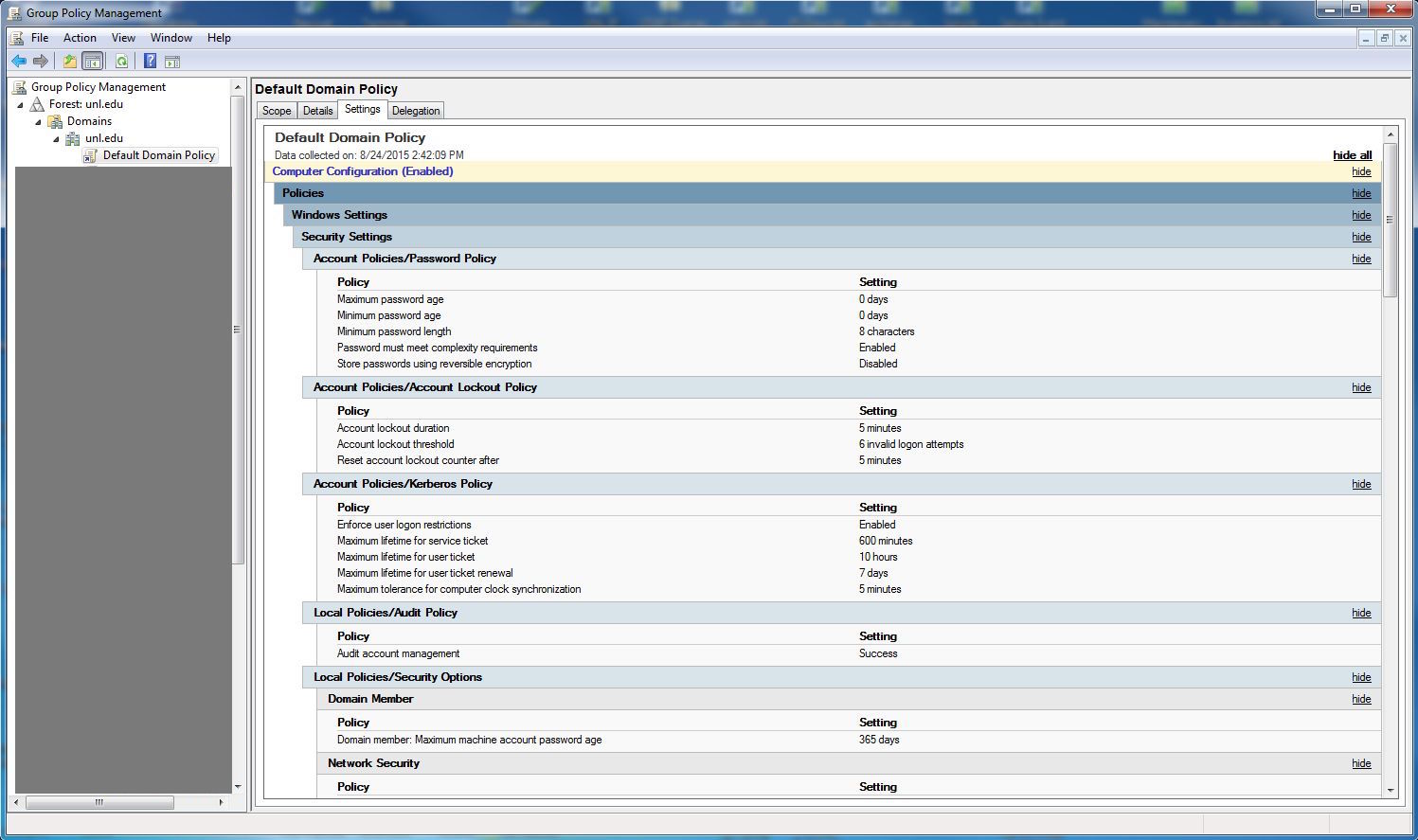
Account Lockout Timing
Active Directory
Active Directory is configured to limit accounts to 6 failures in 5 minutes, with a lockout duration of 5 minutes. This is stored in the Default Domain Policy. Password failures are synchronized across all domain controllers, so the maximum number of failures is 6 in a 5 minute period.
LDAP
LDAP is configured to limit accounts to 6 consecutive failures, with a lockout duration of 5 minutes. This is stored in the dc=unl,dc=edu,ou=policies,cn=default entry:dn: cn=default,ou=policies,dc=unl,dc=eduPassword failures are not synchronized across the 4 LDAP servers, so the maximum number of consecutive attempts is 6*4=24 in a 5 minute period.
objectClass: person
objectClass: pwdPolicy
objectClass: top
cn: default
pwdAttribute: userPassword
pwdLockout: TRUE
pwdLockoutDuration: 300
pwdMaxFailure: 6
Credentials are synchronized across both Active Directory and LDAP, resulting in 30 possible password attempts in a 5 minute period.
Monitoring Authentication Failures
Authentication attempts are monitored using an Authentication Failure Counter, as described in the Internet2 Wiki: https://spaces.internet2.edu/display/InCAssurance/Failed+Authentication+Counter+StrawmanAuthentication failures are tracked for the two authentication stores (Active Directory and LDAP), via our Splunk log aggregation system. Once authentication failures are collected in the Splunk Indexer (Accumulator), a script runs every 10 minutes to monitor the failed authentication attempts and password resets. Authentication failures and password resets are stored in the Authentication Failure Monitor database, which is replicated in two locations. In that 10 minute period, a single user may have had 60 attempts across AD & LDAP.
The code for the authentication failure monitor is available on GitHub: https://github.com/saltybeagle/AuthNFailures
Three searches are monitored:
Grouper is used to monitor the Authentication Failure Database, and synchronize the list of users that have a credential which meets the Bronze credential requirements. A user must have a password reset event stored in the Authentication Failure Database, and have had no more than 10,000 authentication failures, to be included in the Bronze credential group.
The Grouper Loader Job runs every 6 hours via a START_TO_START_INERVAL.

Assurance Degradation
Users must reset their password, and after 10,000 invalid credential attempts their Bronze Assurance will be removed.
After re-establishing their identity using the process defined in 4.2.4.3, Bronze Assurance will be restored.
Entropy Calculation
Per the US Government Password Entropy Calculator (Entropy Spreadsheet, v2.0.0.xls), if the system terminates the account (or assurance) after 16,384 or fewer failed attempts, these parameters meet the Level of Assurance (1 chance in 1,024).